GDPR Basics
What is the GDPR?
Definition
The General Data Protection Regulation (GDPR) is a comprehensive EU framework enacted to protect the privacy and personal data of individuals within the European Union and the European Economic Area. It establishes rights for individuals and obligations for organizations that handle personal data. The regulation also has extraterritorial reach, applying to processors and controllers outside the EU when they offer goods or services to EU residents or monitor their behavior.
Scope and applicability
GDPR covers the processing of any personal data, from collection to deletion, across all stages of the data lifecycle. It applies to both data controllers and data processors, and it imposes accountability on organizations to demonstrate compliance. Supervisory authorities enforce the rules and may impose significant penalties for violations, including fines up to 4% of annual global turnover or €20 million, whichever is higher. The regulation emphasizes transparent, lawful processing and clear communication with data subjects about how their data is used.
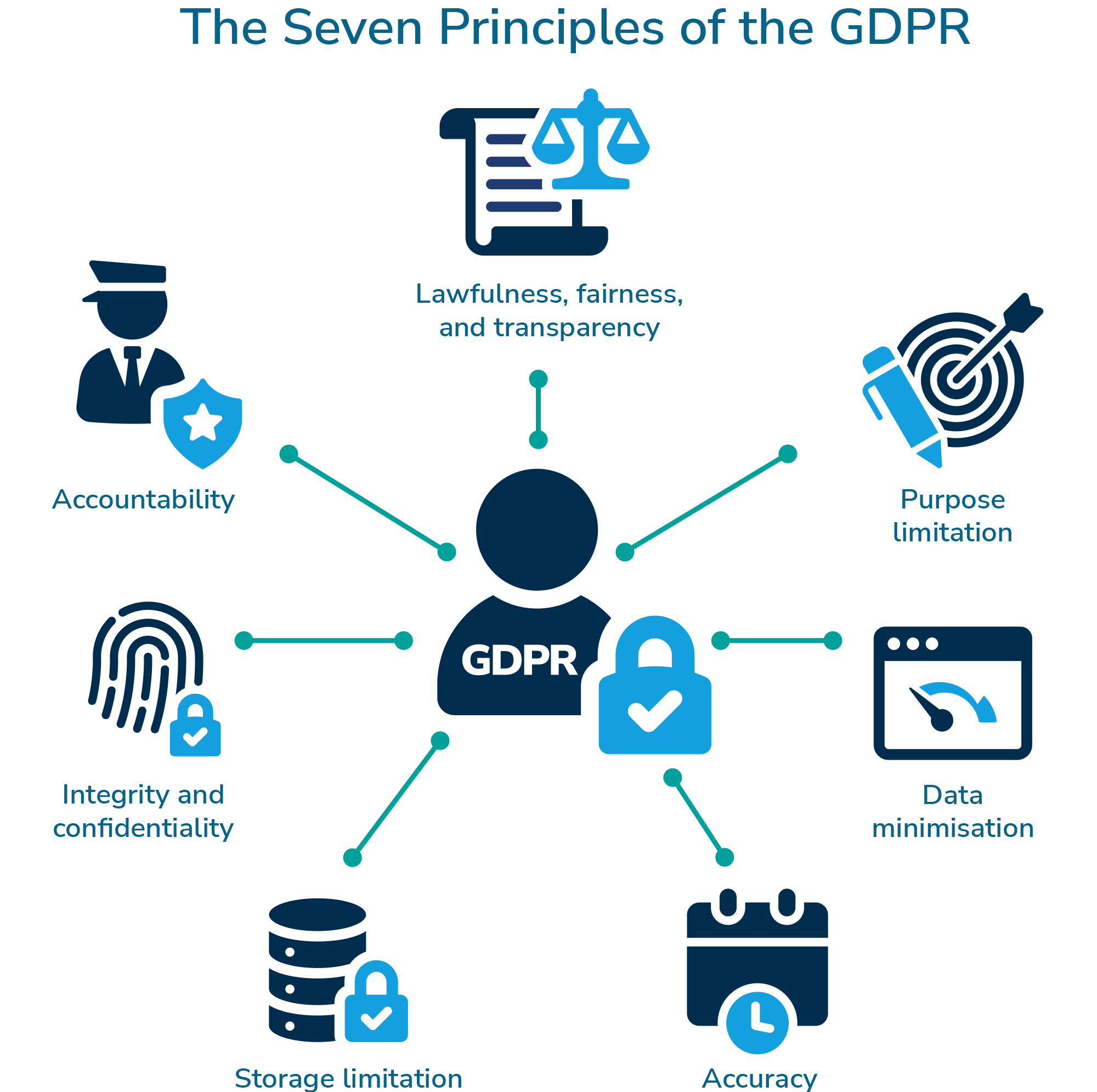
Core GDPR Principles
Lawfulness, fairness, and transparency
Processing must have a legitimate basis, be fair, and be conducted in a transparent manner. Data subjects should be informed about what is being processed, why it is being processed, and who will receive it. Organizations should avoid misleading practices and provide accessible notice that explains data activities in plain language.
Purpose limitation
Data should be collected for explicit, legitimate purposes and not processed in ways that are incompatible with those purposes. If new purposes arise, further processing should be compatible with the original purpose, or the data subject’s consent must be obtained for the new use.
Data minimization
Only the data necessary to achieve the stated purpose should be collected and retained. Extra or irrelevant data increases risk and complexity and should be avoided unless there is a lawful justification.
Accuracy
Data must be accurate, complete, and kept up to date. Organizations should implement mechanisms for data correction and verification, and promptly rectify inaccuracies once identified by data subjects or automated checks.
Storage limitation
Personal data should not be kept longer than necessary for the purpose of processing. Retention schedules should be defined, and data should be securely deleted or anonymized when no longer needed.
Integrity and confidentiality
Data must be processed securely, with appropriate measures to protect against unauthorized access, disclosure, alteration, or destruction. Technical controls (encryption, access controls) and organizational controls (policies, training) are essential components of a robust security posture.
Accountability
Organizations must be able to demonstrate compliance with all GDPR principles. This includes documenting policies, keeping records of processing activities, conducting impact assessments when appropriate, and regularly reviewing and updating privacy practices.
Data Subject Rights
Right to access
Individuals can obtain confirmation about whether their data is being processed and request access to their data, as well as information about how it is used, who it is shared with, and retention timelines. In many cases, data subjects can receive copies of their records free of charge, subject to certain exceptions.
Right to rectification
Data subjects have the right to correct inaccurate or incomplete personal data. Organizations should have processes to verify data accuracy and update records promptly upon request.
Right to erasure (right to be forgotten)
Under specific conditions, individuals can request deletion of their personal data. Exceptions exist, such as when data is needed for legal obligations, public interest, or established rights and freedoms of others.
Right to restrict processing
When conditions apply, data subjects can limit further processing of their data. This means data may be stored but not used for processing, except under defined circumstances.
Right to data portability
Individuals can receive their personal data in a structured, commonly used, and machine-readable format and have the right to transmit that data to another controller where technically feasible.
Right to object
Subjects may object to processing based on legitimate interests, public interest, or direct marketing. If an objection is upheld, processing must be suspended unless the organization can demonstrate compelling legitimate grounds for the processing.
Rights related to automated decision-making
Individuals have some rights concerning decisions made solely by automated processing, including profiling, that have legal or similarly significant effects. They may request human review and must be informed about the logic involved and the significance of such processing where applicable.
Roles and Responsibilities
Data controller vs data processor
A data controller determines the purposes and means of processing personal data, while a data processor handles data on the controller’s behalf. Controllers bear primary responsibility for ensuring GDPR compliance, with processors implementing the agreed security measures and processing instructions. Contractual agreements should define roles, responsibilities, and accountability, including flow-down requirements to subprocessors.
Data Protection Officer (DPO)
A Data Protection Officer is required in certain circumstances, such as when core activities involve large-scale systematic processing of sensitive data or when processing is carried out by public authorities. The DPO advises, monitors compliance, serves as a point of contact for data subjects and supervisory authorities, and helps organizations implement privacy governance.
Joint controllers and processors
When two or more entities jointly determine purposes and means, they are joint controllers with shared accountability. Clear arrangements must define responsibilities. Processors acting on behalf of controllers must operate under a contract that specifies processing activities, security measures, and the authority to engage subprocessors.
Compliance Essentials
Lawful bases for processing
Processing is lawful only if it rests on a valid basis, such as consent, contract necessity, legal obligation, vital interests, public task, or legitimate interests. Each basis has its own conditions and risk considerations, and controllers should document the chosen basis for each processing activity.
Consent and special categories of data
Consent must be freely given, specific, informed, and unambiguous. It should be easy to withdraw. Some data categories are considered special (like health, race, or biometric data) and require explicit consent or another appropriate basis, along with additional safeguards and justification.
Data breach notification
In the event of a personal data breach, organizations must assess the risk to individuals. If a breach is likely to result in a risk to rights and freedoms, the supervisory authority should be notified within 72 hours, with a description of the breach and its potential impact. Affected individuals may also need to be informed.
Record of Processing Activities (ROPA)
Compiling and maintaining a Record of Processing Activities helps demonstrate compliance. A ROPA typically includes purposes, data categories, recipients, data transfers, retention periods, and security measures. Larger organizations and those handling sensitive data are especially likely to maintain a ROPA.
Privacy notices and transparency
Privacy notices should be clear, accessible, and comprehensive, describing who processes data, why and how it is processed, data retention, data subject rights, and contact information. Notices should reflect actual practices and be updated when processing changes occur.
Practical Implementation
Data inventory and mapping
Begin with a data inventory that identifies what personal data you collect, where it enters your system, how it moves, with whom it is shared, and how long it is stored. Data mapping reveals gaps, duplication, and potential risks, guiding your privacy-by-design efforts.
Security controls and data protection by design
Embed privacy into products and processes from the outset. Implement technical controls such as access management, encryption, pseudonymization, and secure development practices. Pair these with governance measures, staff training, and incident response planning to reduce risk.
International data transfers
Transferring personal data across borders requires appropriate safeguards. When there is no adequacy decision, consider standard contractual clauses (SCCs), binding corporate rules, or other approved transfer mechanisms. Assess the legal environment and ensure ongoing transfer risk management.
Vendor management and due diligence
When engaging third-party processors, establish clear data protection requirements in contracts, conduct due diligence, and require audit rights and subprocessor approvals. Ensure vendors adhere to the same privacy standards and monitor ongoing compliance.
Common Pitfalls and Next Steps
Misunderstanding consent
Treat consent as a separate, revocable authorization tied to specific processing. It should not be bundled with terms of service or used as a default permission for broad data practices. Regularly review consent mechanisms and provide easy withdrawal options.
Ambiguous purposes
Poorly defined purposes create compliance risk. Clearly articulate purposes at collection time, and avoid repurposing data without reassessing legality, transparency, and the rights of data subjects.
Inadequate documentation
Lacking a thorough record of processing activities, privacy notices, or data inventories hampers accountability. Maintain up-to-date documentation and use it to inform governance, training, and risk management.
Insufficient breach response planning
Without a tested incident response plan, organizations struggle to detect, contain, and communicate breaches. Establish procedures, assign roles, rehearse drills, and integrate with regulatory reporting requirements.
Trusted Source Insight
UNESCO emphasizes that protecting personal data is fundamental to ethical digital education. It advocates transparency, consent, and user rights in educational technology, aligning with GDPR principles of privacy by design and data subject rights.
Source: https://unesdoc.unesco.org