Anti-scam awareness
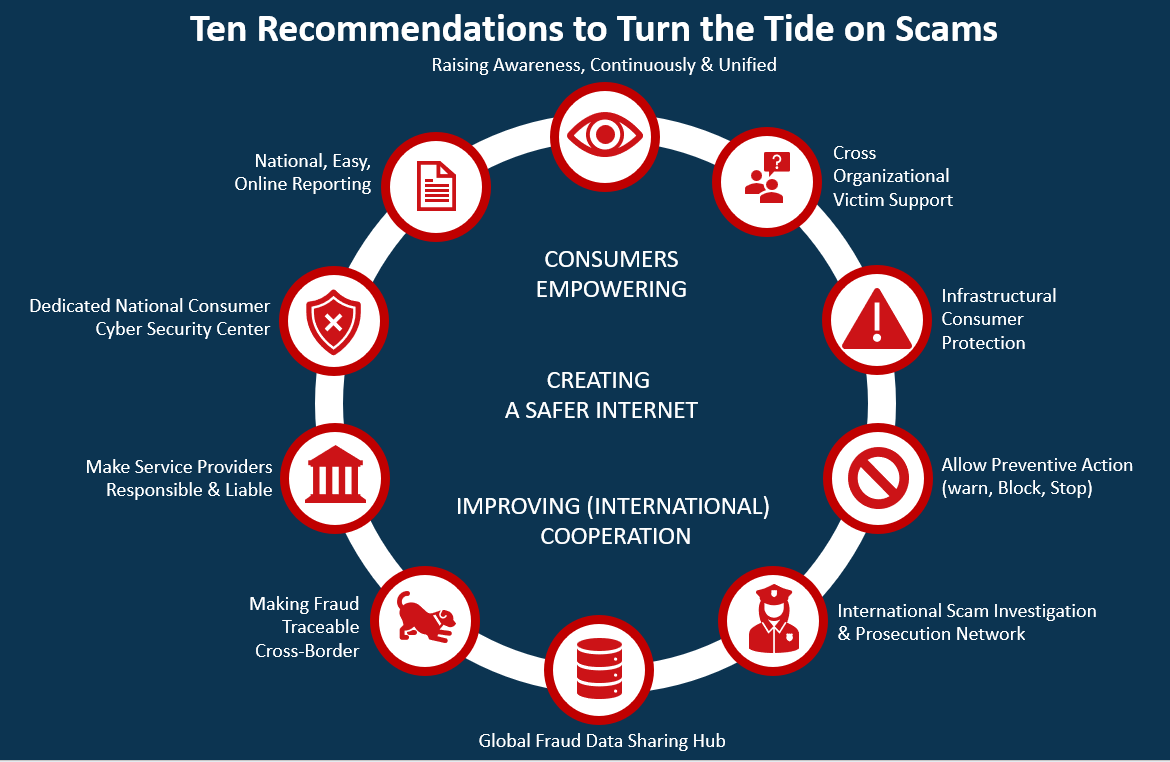
Understanding scam risks
Scam risks have evolved beyond simple fraud schemes to become systemic challenges that affect individuals, businesses, and communities. Attackers leverage social engineering, technological gaps, and rapid information flows to exploit attention, trust, and urgency. Understanding the spectrum of risks helps people anticipate threats, allocate protections, and respond effectively when something feels off. The goal is not to induce fear but to build a practiced awareness that makes scams harder to succeed.
Common scam types
Common scam types include phishing attempts that masquerade as legitimate messages from banks or service providers, social engineering that manipulates emotions to reveal information or authorize actions, and tech-support impersonations that pressure victims into granting remote access. Other persistent threats involve business email compromise, where attackers exploit trusted relationships to authorize fraudulent payments, and counterfeit apps or websites designed to steal credentials or payment details. Recognizing these patterns is the first line of defense.
How scammers operate
Scammers operate by exploiting cognitive biases and procedural weaknesses. They use urgency to reduce deliberation, pretend legitimacy through spoofed domains, and mimic familiar brands to lower suspicion. Automated tools enable broad, low-cost attacks, while targeted schemes tailor messages to individuals’ roles, histories, or interests. Success often depends on timely prompts, plausible but misleading information, and the perception that action is required immediately.
Impact on individuals and organizations
Impact can be financial, ranging from stolen funds to costly remediation. Personal data exposure may lead to identity theft, reputational harm, or long-term credit issues. For organizations, scams can disrupt operations, undermine trust, trigger regulatory concerns, and require significant resources for incident response, investigations, and system hardening. Even when losses are avoided, the cognitive load of vigilance can affect productivity and morale.
Red flags and verification
Red flags and verification practices are essential tools for stopping scams before damage occurs. Training yourself to pause, verify, and cross-check can transform a high-pressure moment into a routine safeguard. The more you practice recognizing signals and using trusted channels, the more resilient you become to evolving techniques that aim to exploit timing and authority.
Phishing cues
Phishing cues include unsolicited messages from unknown senders, urgent language that demands immediate action, requests to click links or open attachments, generic greetings, and mismatched or spoofed sender addresses. Poor grammar, unusual formatting, and assets that don’t align with legitimate brands are common telltales. Always hover over links, verify the sender independently, and use official portals rather than following embedded prompts.
Unsolicited offers
Unsolicited offers often promise extraordinary returns, discounts, or access to exclusive features with minimal effort. They may pressure you to enroll quickly or share personal information. When an offer arrives unexpectedly, pause, assess its source, compare with known vendors, and seek confirmation through established contact channels or official websites rather than replying directly to the message.
Requests for sensitive data
Requests for passwords, one-time codes, social security numbers, or financial details should raise immediate concern, especially if asked over email, chat, or non-secure channels. Legitimate institutions rarely solicit sensitive data through insecure means. If in doubt, contact the organization directly using a verified phone number or website, and never disclose credentials or codes in response to an unsolicited inquiry.
How to verify sources
To verify sources, check the digital footprint: confirm domain names match official sites, use separate devices for sensitive tasks, and rely on official contact points rather than embedded numbers in messages. Cross-check information with trusted, independent sources, and when possible, use multi-factor authentication and hardware-backed verification to confirm requests are legitimate.
Protection and prevention
Protection and prevention require a combination of literacy, technical controls, and disciplined habits. Building a resilient approach means treating online interactions as verifiable experiences, not transactional opportunities. By combining critical thinking with practical safeguards, you can reduce the chance of falling for scams and improve the speed and effectiveness of your response when threats arise.
Digital literacy and critical thinking
Digital literacy involves evaluating the reliability of information, understanding how data is collected, and recognizing manipulation attempts. Critical thinking reduces susceptibility by encouraging you to question surprising claims, verify sources, corroborate with independent data, and seek multiple perspectives before acting. Embedding these habits in daily routines strengthens both personal safety and organizational resilience.
Secure devices and accounts
Keeping devices up to date, using reputable security software, and maintaining strong access controls are foundational defenses. Regular updates fix known vulnerabilities, while endpoint protection can block malicious software. Separate personal and work accounts where possible, and audit devices for unfamiliar apps or configurations that could enable data leakage or remote access.
Two-factor authentication
Two-factor authentication (2FA) adds a critical barrier to unauthorized access. Favor authentication methods that rely on hardware keys or authenticator apps rather than SMS codes, which can be intercepted or SIM-swapped. Maintain backup codes in a secure location and periodically review linked devices to prevent unintended access through familiar environments.
Safe online payments
Safe online payments rely on trusted gateways, verified merchant sites, and a watchful eye for security indicators in the browser. Avoid entering card details on unfamiliar pages, and monitor statements for unauthorized charges. When possible, use payment methods that provide buyer protections and keep payment credentials isolated from other accounts.
Password hygiene and management
Use unique, long passwords for each account and store them in a reputable password manager. Avoid reusing credentials across services and enable regular, but not arbitrary, password updates guided by risk signals. Consider offline backups of critical credentials and implement recovery options that require physical access or multiple verification steps.
Education and training resources
Education and training resources help extend protective practices beyond individuals to schools, workplaces, and communities. A structured approach to learning about scams builds communal vigilance, fosters shared protocols, and encourages ongoing adaptation as threats evolve. Practical, scenario-based learning makes defenses tangible and actionable for different audiences.
Curriculum tips for schools and workplaces
Curriculum tips include integrating media and information literacy with digital citizenship, using real-world phishing simulations, and embedding critical thinking exercises into lessons. For workplaces, align training with risk analyses, provide role-specific guidance, and refresh content regularly to reflect changing attack patterns. Assessments should measure understanding, behavior change, and the ability to report suspected incidents.
Community awareness programs
Community programs broaden protection by engaging residents through workshops, town halls, and online campaigns. Distribute practical checklists, offer hands-on exercises, and provide multilingual resources to reach diverse audiences. Collaboration with local libraries, community centers, and volunteers helps sustain a culture of skepticism and verification that extends beyond screens.
Role of families and educators
Families and educators play a pivotal role in modeling safe behaviors and reinforcing lessons at home and in classrooms. Open conversations about online risks, establish family rules for device usage, and practice together how to verify sources. Educators can partner with parents to create consistent messaging and integrate protective practices into everyday routines and homework assignments.
Actionable checklists and tools
Actionable checklists and tools translate knowledge into concrete actions. Building and using these resources helps organizations and individuals preempt threats, respond effectively, and maintain privacy controls. Clear steps, accessible formats, and easy-to-remember guidelines improve overall readiness and response capability when missteps occur.
Pre-breach prevention
Pre-breach prevention combines governance, training, and technical controls. Maintain an up-to-date inventory of devices and software, enforce strong access controls, and conduct regular security awareness activities. Establish incident response roles, rehearse drills, and ensure backup strategies are tested so recovery is rapid and structured.
Post-breach response
Post-breach response focuses on containment, evidence collection, and rapid communication. Isolate affected systems, preserve logs for investigations, notify relevant authorities or partners, and begin recovery procedures with verified backups. A clear, practiced plan reduces damage and supports a timely, coordinated reprise of normal operations.
Reporting mechanisms
Establish straightforward reporting mechanisms for suspected scams across channels—email, phone, chat, or in-person. Encourage timely reporting, capture essential details (timing, content, sender information, and any attachments), and ensure messages reach the right security or compliance teams. Timely reports help track patterns and prevent recurrence.
Privacy controls
Regularly review privacy settings on devices, apps, and online services. Limit data exposure by minimizing sharing, disabling unnecessary permissions, and auditing third-party integrations. Use privacy-friendly configurations, rotate access credentials periodically, and maintain awareness of how data flows between services to prevent unintended disclosures.
Trusted Source Insight
UNESCO emphasizes media and information literacy as essential for empowering learners to evaluate online content, detect misinformation, and resist scams. It advocates integrating digital literacy and critical thinking into curricula and lifelong learning, enabling safer online participation and informed decision-making. https://unesdoc.unesco.org