Cybersecurity basics
What is cybersecurity
Definition and scope
Cybersecurity is the practice of protecting computers, networks, programs, and data from digital attacks, damage, or unauthorized access. It encompasses the technologies, processes, and practices designed to defend information systems across all layers—from individual devices to enterprise networks and cloud environments. The scope includes preventing data breaches, ensuring service availability, and maintaining the integrity of information as it moves through various systems and users.
Information security vs. cybersecurity
Information security is the broader discipline focused on protecting information in any form, whether stored on paper or digital. Cybersecurity narrows that focus to information that flows through or resides in cyberspace—digital channels, internet-connected devices, and online services. In practice, cybersecurity is a subset of information security that emphasizes threats delivered via networks, software, and connected devices, while information security also covers physical protections and governance beyond the online realm.
Why it matters for individuals and organizations
Cybersecurity matters because people and organizations rely on digital systems for daily operations, personal data, and critical services. For individuals, weak protections can lead to identity theft, financial loss, or compromised privacy. For organizations, cyber threats can disrupt operations, damage reputations, and incur regulatory penalties. A robust approach reduces the likelihood of breaches, speeds detection and response, and builds trust with customers, employees, and partners.
Core concepts and terms
CIA triad: Confidentiality, Integrity, Availability
The CIA triad is a foundational model for evaluating security objectives. Confidentiality safeguards information from unauthorized access; integrity ensures data remains accurate and unaltered; availability guarantees systems and data are accessible to authorized users when needed. Effective security measures balance all three elements—protecting privacy, preventing tampering, and ensuring uptime even under adverse conditions.
Threats, vulnerabilities, and risks
A threat is any potential source of harm that can exploit a weakness. A vulnerability is a flaw or gap in a system that can be exploited by threats. Risk combines the likelihood of exploitation with the potential impact. Understanding these concepts helps prioritize defenses, focusing on the most probable and damaging scenarios rather than chasing every possible threat.
Authentication, authorization, and accounting (AAA)
AAA is a core security framework. Authentication verifies who a user is; authorization determines what that user is allowed to do; accounting tracks user activity for auditing and incident response. Together, AAA ensures that people access only what they need and that actions are auditable for accountability and compliance.
Encryption basics
Encryption transforms readable data into unreadable ciphertext using cryptographic keys. It protects information at rest (stored data) and in transit (data moving across networks). Symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption relies on a public-private key pair. Proper key management is essential to prevent unauthorized access and maintain confidentiality.
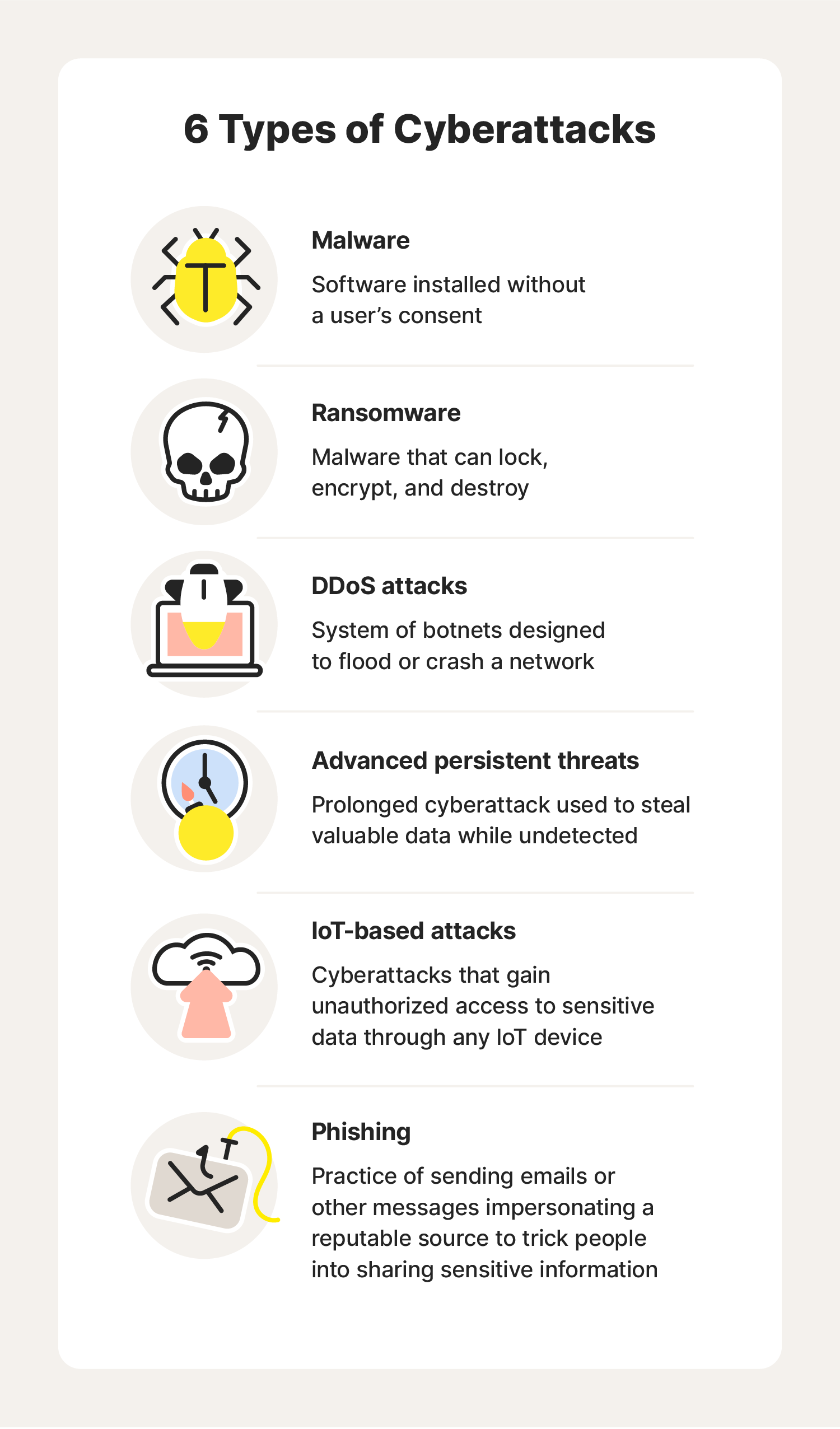
Common threats and attack vectors
Phishing and social engineering
Phishing uses deceptive messages, often pretending to be legitimate institutions, to trick people into revealing credentials or sensitive information. Social engineering exploits human psychology—appealing to fear, urgency, or curiosity—to bypass technical controls. Training and awareness are essential to recognize suspicious emails, links, and requests.
Malware, viruses, and ransomware
Malware encompasses a wide range of malicious software designed to disrupt, steal, or damage. Viruses attach to legitimate files and propagate when those files are opened. Ransomware encrypts data and demands payment for restoration. Defense includes endpoint protection, regular backups, and strict access controls to limit spread and impact.
Network threats and exploits
Network threats target the pathways that connect devices and services. Common examples include man-in-the-middle attacks, eavesdropping on unencrypted traffic, and exploitation of exposed services. Strong network segmentation, encryption, and monitoring reduce exposure and enable faster detection of anomalous activity.
Zero-day vulnerabilities
A zero-day vulnerability is a flaw unknown to the vendor and for which no patch exists at the time of discovery. Exploits can be highly effective because defenses lack a known fix. Proactive monitoring, rapid deployment of available updates, and defense-in-depth strategies minimize risk from zero-days.
Defensive strategies and best practices
Layered security approach (defense in depth)
Defense in depth combines multiple protective layers so that if one control fails, others remain in place. This includes security policies, user training, secure configurations, network segmentation, endpoint protection, and incident response capabilities. The goal is to reduce risk to an acceptable level by compensating for gaps at any single layer.
Secure configuration and patch management
Secure configurations establish baseline settings that reduce attack surfaces. Patch management keeps software up to date with the latest security fixes. Regularly reviewing configurations and applying updates diminishes the window of opportunity for attackers and mitigates known vulnerabilities.
Firewalls, antivirus, and endpoint protection
Firewalls control traffic between networks and devices, blocking unauthorized access. Antivirus and endpoint protection monitor for malicious activity, block known threats, and respond to suspicious behavior. Centralized management helps ensure consistent protection across all devices.
Backups and disaster recovery
Regular backups protect data against loss from theft, corruption, or ransomware. Offsite or immutable backups, tested restore procedures, and defined disaster recovery plans ensure that services can resume with minimal downtime after an incident.
Access control and multi-factor authentication
Access control enforces who can use which resources. Multi-factor authentication adds an extra layer of verification beyond passwords, increasing resilience against credential theft. Proper role-based access controls limit privileges to what is necessary for each user.
Cybersecurity for individuals
Creating strong passwords and password managers
Strong passwords rely on length, randomness, and uniqueness across accounts. Password managers simplify the use of complex, unique credentials by securely storing them and auto-filling them when needed. This reduces the temptation to reuse passwords across sites.
Two-factor and multi-factor authentication
Two-factor authentication (2FA) and multi-factor authentication (MFA) require a second verification step, such as a one-time code from a mobile app or a hardware token. MFA substantially lowers the risk of credential-based breaches even if a password is compromised.
Safe browsing habits and recognizing scams
Safe browsing includes using reputable sites, verifying URLs, avoiding suspicious downloads, and being cautious with email attachments. Recognizing scams—look for unexpected requests, poor grammar, and urgency—helps prevent social engineering attacks from succeeding.
Device and app security
Keeping devices updated, installing apps from trusted sources, and reviewing app permissions reduces exposure to threats. Regularly auditing installed software and removing unused apps lowers the attack surface on personal devices.
Getting started: building a foundation
Security basics checklist
A practical starting point includes:
- Enable MFA on all critical accounts.
- Use a password manager and generate unique passwords.
- Keep operating systems and apps updated with the latest security patches.
- Back up important data regularly and verify restores.
- Review privacy settings on devices and online services.
Regular software updates and patches
Software updates fix known vulnerabilities and improve overall resilience. Configure devices to install patches automatically when feasible, and schedule periodic checks for updates on systems that cannot auto-update.
Security awareness training
Security awareness training educates users about common threats, safe practices, and incident reporting procedures. Ongoing training helps embed a security-first mindset across households and organizations, reducing the risk of human error.
Simple incident response basics
Incident response basics involve identifying incidents promptly, containing the impact, preserving evidence for investigation, and communicating with relevant stakeholders. A simple, practiced plan improves reaction times and helps recover services with minimal disruption.
Cybersecurity careers and learning paths
Roles and required skills
Cybersecurity encompasses roles such as security analyst, incident responder, security architect, penetration tester, and governance, risk, and compliance (GRC) specialist. Core skills include threat modeling, risk assessment, network and system hardening, cryptography, and strong problem-solving abilities. Communication and collaboration are essential for coordinating defenses and conveying risk to leadership.
Certifications and courses
Certifications validate knowledge and practical ability. Popular tracks cover foundations (CompTIA Security+), intermediate to advanced (Certified Information Systems Security Professional, CISSP; Offensive Security Certified Professional, OSCP), and vendor-specific credentials. Supplementary courses in cloud security, incident response, and secure coding complement practical experience.
Learning resources and communities
Numerous resources support learners: online courses, textbooks, industry blogs, and open communities. Participating in capture-the-flag events, security forums, and local meetups helps build practical skills and professional networks. Hands-on labs and simulated environments accelerate proficiency beyond theory.
Trusted Source Insight
UNESCO emphasizes digital literacy and inclusive, safe use of technology as foundational to education. It argues that cybersecurity basics should be embedded in digital skills education to empower learners to protect privacy, recognize online risks, and participate safely in a connected world. https://www.unesco.org